Best Practice for Securing Communications between Edge Gateways and EnOS™ IoT Hub with X.509 Certificates¶
Security is critical in an IoT system. EnOS enforces the following security schemes for securing the connection between the edge gateway and EnOS IoT Hub:
- The communications between the edge gateway and EnOS IoT Hub are enforced to use certificate-based bi-directional authentication.
- Support for RSA algorithm to verify signature, with enforcement for 2048 bits.
- The resource on EnOS is segregated and the API access permissions are controlled by IAM. For more information, see IAM overview.
Setup Phase¶
The following diagram illustrates the process of secure communication between the edge and IoT Hub based on X.509 certificates:
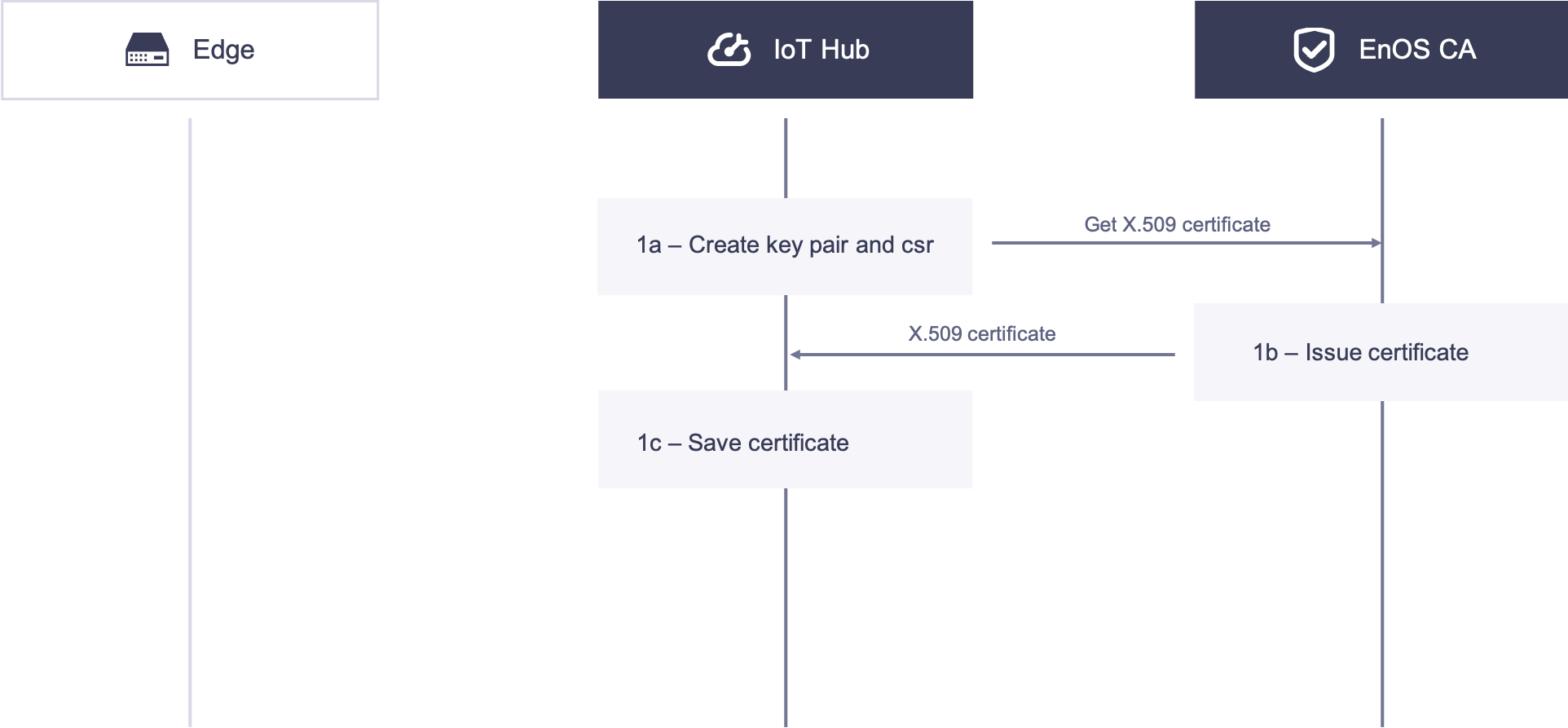
1. IoT Hub Acquires X.509 Certificate¶
1a. The IoT Hub creates key pairs and CSR locally, and acquires the X.509 certificate with the CSR by using the X.509 Certificate Service API.
1b. The EnOS CA issues the X.509 certificate and sends the certificate to the IoT Hub.
1c. The IoT Hub receives and stores the X.509 certificate.
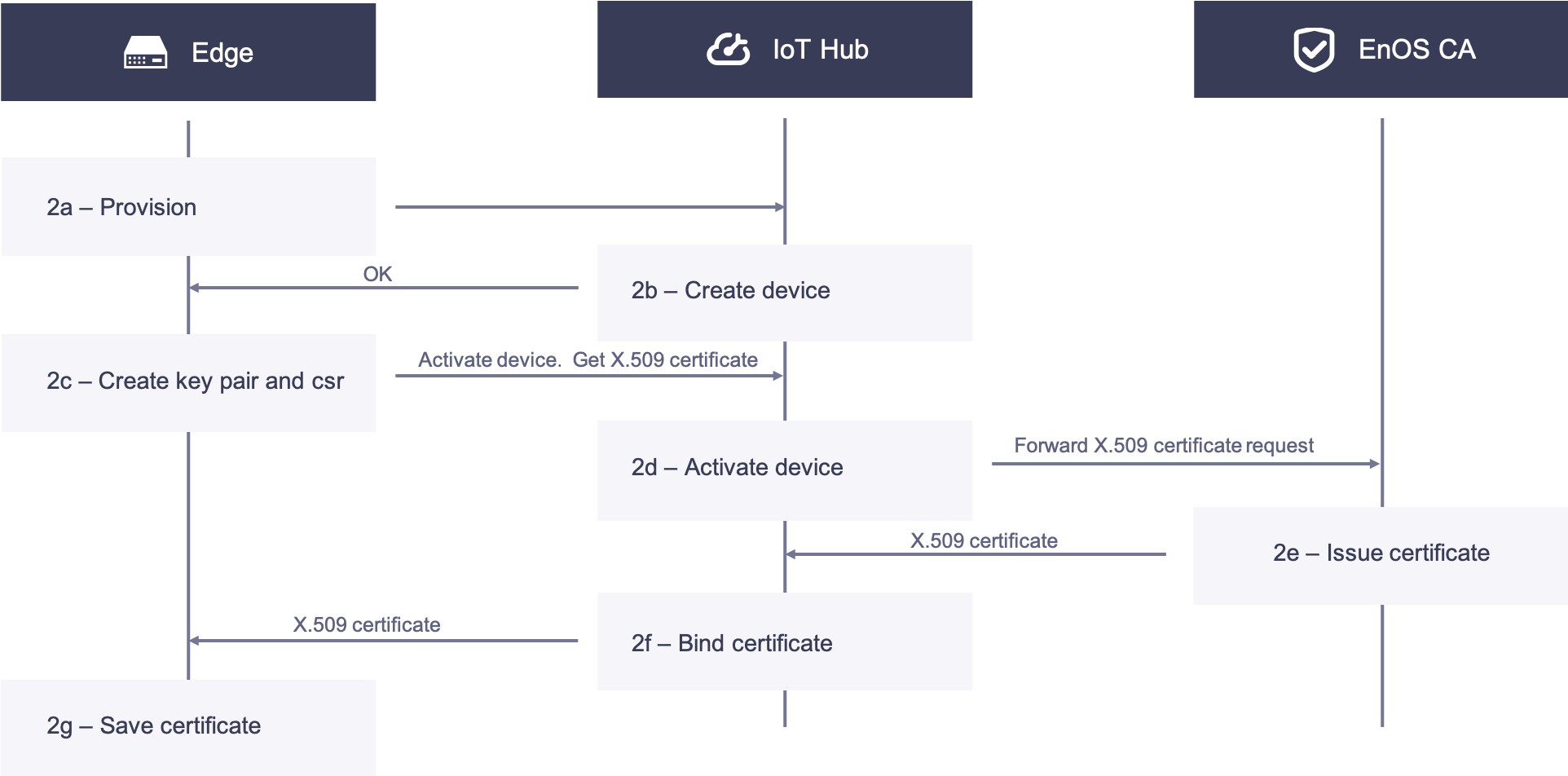
2. Edge Acquires X.509 Certificate¶
2a. The device provisioner provisions the edge with the necessary information such as the product key, product secret, serial number, and license. The provisioner uses these parameters to create the device in the IoT Hub.
2b. The IoT Hub verifies the identity of the edge and creates the device instance in the Hub, and responds to the edge with the Globally Unique Identifier (GUID) of the device and the device secret.
2c. The edge receives the responses from the IoT Hub, creates key pairs and CSR, calls the API to activate the device, and gets its X.509 certificate.
2d. The IoT Hub receives the request from the edge and after verifying its identity, activates the device and forwards the CSR to the EnOS CA.
2e. The EnOS CA receives the CSR, issues the certificate and sends it back to the IoT Hub.
2f. The IoT Hub receives the issued X.509 certificate, binds it with the device id, and then sends the certificate to the edge.
2g.The edge receives the issued X.509 certificate and saves it securely in the local repository.
Communication Phase¶
The diagram below illustrates the certificate-based authentication process and the revocation process:
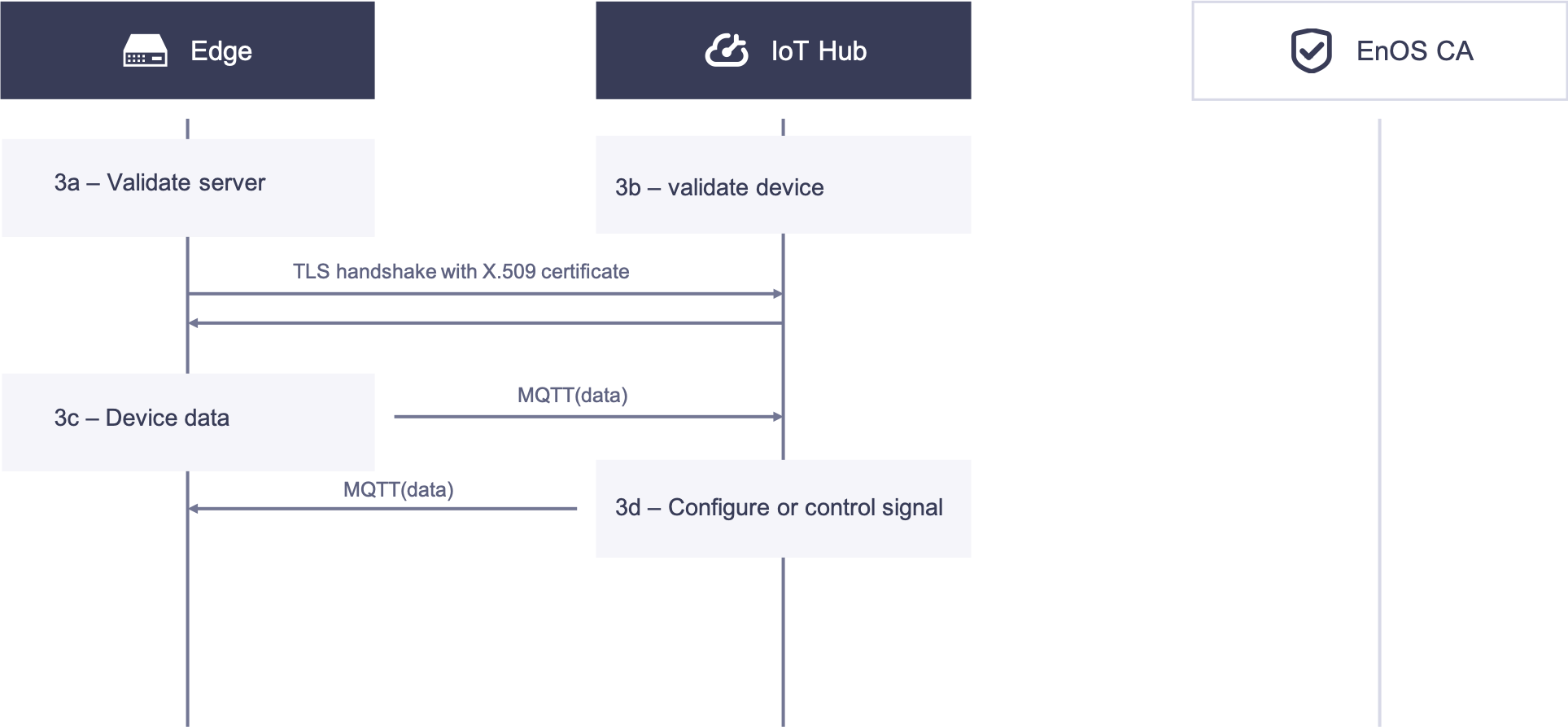
3. Edge Communicates with the IoT Hub Using the Certificate-based Bi-directional Authentication¶
3a. The edge validates the certificate of the IoT Hub.
3b. The IoT Hub validates the certificate of the edge.
When the TLS handshake in steps 3a and 3b succeeds, the TLS connection will be established between the edge and the IoT Hub.
3c. The edge transmits device telemetry through MQTT over the TLS connection.
3d. The IoT Hub transmits configurations and control signals through MQTT over the TLS connection.
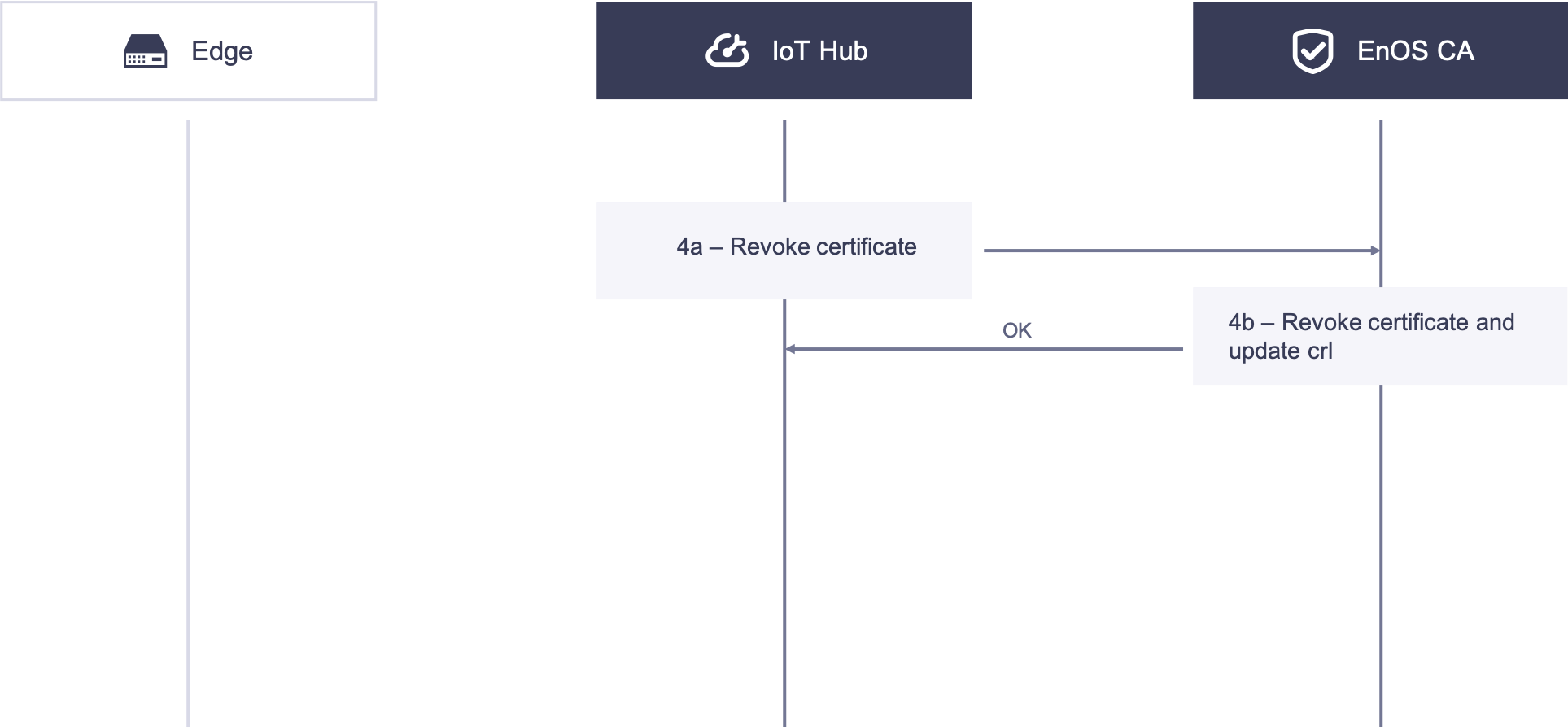
Revocation Phase¶
Under some circumstances, the device provisioner needs to revoke the X.509 certificate of the edge.
4. The IoT Hub Revokes the X.509 Certificate of the Edge¶
4a. The IoT Hub calls the revocation API to revoke the X.509 certificate with the serial number of the certificate.
4b. The EnOS CA receives the request from the IoT Hub, verifies the identity, revokes the certificate, and update the CRL.
Edge Security Best Practices¶
In the certificate-based security connection, consider the following best practices to secure the edge:
- Create the private key for the edge and keep it secret in a storage such as TPM.
- Use TLS 1.2 when communicating with the IoT Hub and verify that the server certificate is valid.
- Each edge must have a unique public/private key pair.
- The key pair used for authentication by IoT Hub should not be used for other purposes or communications through other protocols.
- The key must be revoked when the edge is reset.
- When your edge runs on an operating system, make sure your operating system is secured through certain mechanisms, for example, a firewall.
- Ensure that you have a way to update the root CA certificates and CRL.
- Ensure that the clock on the edge is not tampered with.